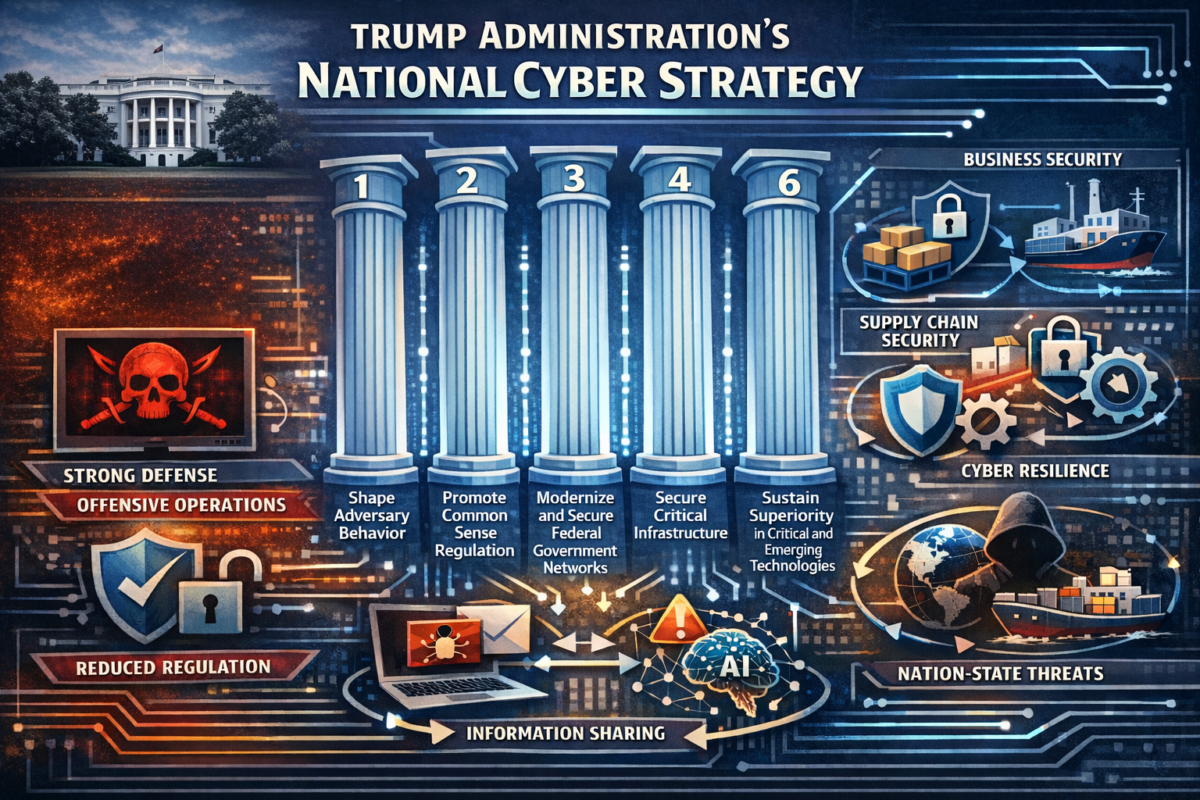
On March 6, 2026, the White House released President Trump’s Cyber Strategy for America (the “Strategy”), a directional statement of the Administration’s cybersecurity priorities. The Strategy signals an aggressive posture toward foreign cyber adversaries, a less prescriptive approach to cyber regulation, and a broader effort to protect U.S. technological and infrastructure advantages. For businesses, this may mean that federal cybersecurity…
Debevoise & Plimpton LLP announced the launch of STAAR 2.0, an enhanced version of its award-winning[1] client-facing AI platform designed to help in-house legal and compliance teams evaluate, govern, and deploy artificial intelligence quickly and responsibly. STAAR 2.0 is built with Legora’s Portal architecture, which converts the knowledge gained from five years of advising over 100 clients on complex AI-related…
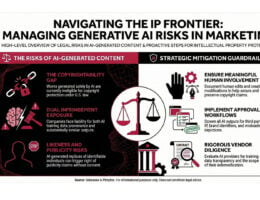
Generative AI tools are now a routine feature of marketing, advertising, and communications workflows. When deployed thoughtfully, these tools have a variety of benefits: reduced costs, accelerated production timelines, and expanded creative capacity. When used without adequate guardrails, AI tools can generate problems just as easily as content: intellectual property risk, reputational harm, and increased regulatory scrutiny. As organizations integrate…
On February 19, 2026, Law360 published an article titled “Meet the Attys ‘Vibe Coding’ Their Own AI Apps,” which features two different AI apps created by Debevoise lawyers and technologists. The first is a game that comes at the end of the firm’s training on its AI policy and tests whether lawyers and staff understand the requirements of the policy.…
Most companies that allow generative AI (“GenAI”) in the workplace have a policy requiring users to check AI outputs to ensure that they are accurate, complete, and fit for purpose. But once an employee reviews the AI output and is comfortable with it, the employee can thereafter circulate that document internally or externally as if they drafted it themselves, without…