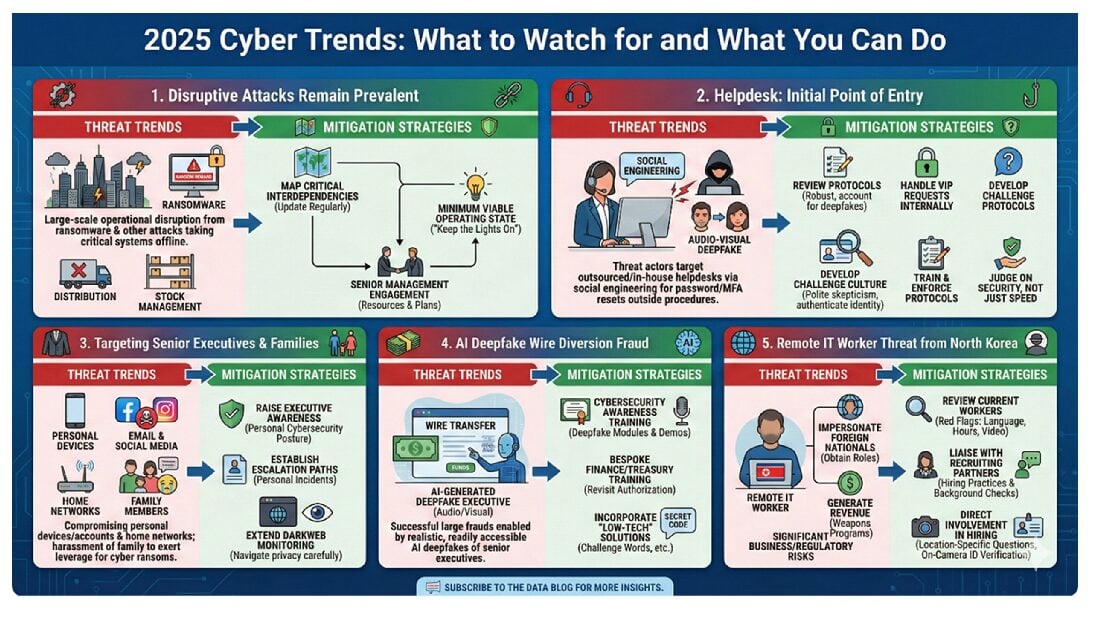
The cyber threat landscape in 2025 was varied with greater ebbs and flows in threat actor activity than in previous years. After a relatively quiet first half, cyberattacks ramped up…
As we approach the end of the year, here are the Top 5 Cybersecurity posts on the Debevoise Data Blog in 2025. 1. Protecting Privilege in Incident Response: Litigation Lessons…
After several years of contentious negotiations, late last year the United Nations General Assembly adopted the UN Convention against Cybercrime (the “UNCC”)the most significant international agreement on cybercrime and electronic…
Overview Companies responding to data breaches are faced with the question of whether their incident response investigation is protected by attorney-client privilege or attorney work-product doctrine. The issue primarily relates…
President Trump issued an Executive Order on June 6, 2025, that sheds light on the Administration’s approach to cybersecurity and AI by highlighting foreign threats to U.S. cybersecurity, emphasizing federal…
All eyes are on the DOJ Bulk Sensitive Data Rule (28 C.F.R. Part 202), and July 8, 2025, when the recently announced good-faith safe harbor expires. The rule, which the…
As AI adoption continues to increase, businesses are looking for familiar risk management protocols for AI governance. One obvious governance framework to use is cybersecurity, which is another area where…
Most companies have implemented protocols for when an employee emails confidential information to the wrong person. A new version of that problem occurs when an employee uploads sensitive information to…
OVERVIEW OF THE NEW LEGISLATION Definitions The new legislation, described as the first Hong Kong cybersecurity law, regulates designated “Operator of Critical Infrastructure” (the “CIO”) and its “Critical Computer Systems”…
On February 20, 2025, the SEC announced the creation of the Cyber and Emerging Technologies Unit (“CETU”) to focus on “combatting cyber-related misconduct and to protect retail investors from bad…